Unusual sign in activity
Author: a | 2025-04-24
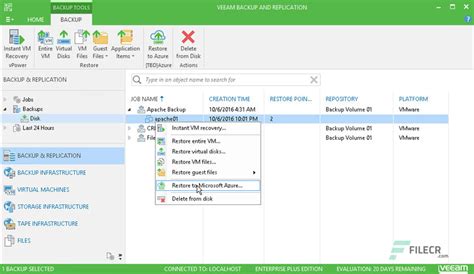
Text presented in the Unusual Sign-in Activity email letter: Subject: Email Account Suspension account Unusual sign-in activity We detected something unusual about a recent sign-in to the I got an unusual sign in activity email from Microsoft from another country and the below is what I got. Session activity Additional verification requested Unusual activity detected Unusual activity detected Resolved unusual activity Successful sign-in. Does this mean that the hacker was able to sign in or did Microsoft prevent them?
Not Unusual unusual sign-in activity and consequent not
Different with your account recently, follow these steps to review your account security: Sign in to the Security basics page for your Microsoft account. Select Review activity to check for any unusual sign-in attempts on the Recent activity page. If you see account activity that you're sure wasn't yours, let us know and we can help secure your account—if it's in the Unusual activity section, you can expand the activity and select This wasn't me. If it's in the Recent activity section, you can expand the activity and select Secure your account. If you think someone else may have accessed your account, go back to the Security basics page and select Change password. Create a strong password that you can remember, and don't share it with anybody else. If you tried to sign in to your account but can't, someone may have changed your password. Follow these steps to get back into your account: Try to reset your password with the instructions listed in When you can't sign in to your Microsoft account. Starting with this step saves you extra effort if you accidentally signed in with a different account than the alert was for. If that doesn't work, try to sign in to your account again. Select Forgot my password on the sign-in page, and then select I think someone else is using my Microsoft account. Follow the instructions to recover your account. See also I think my account's been compromised My username and password have stopped working I can't sign in to my Microsoft account How to keep your Microsoft account safe and secure. Unblock my Outlook.com account Account security tools Need more help? Can't sign in? If you can't sign into your Microsoft account, most issues can be identified by our sign-in helper tool.Sign-in helper Contact Support For technical support, go to Contact Microsoft Support, enter your problem and select Get Help. If you still need help, select Contact Support to be routed to the best support option. Important: To protect your account and its contents, our support agents are not allowed to send password reset links, or access and change account details. Need more help? Want more options? Explore subscription benefits, browse training courses, learn how to secure your device, and more. Text presented in the Unusual Sign-in Activity email letter: Subject: Email Account Suspension account Unusual sign-in activity We detected something unusual about a recent sign-in to the I got an unusual sign in activity email from Microsoft from another country and the below is what I got. Session activity Additional verification requested Unusual activity detected Unusual activity detected Resolved unusual activity Successful sign-in. Does this mean that the hacker was able to sign in or did Microsoft prevent them? AgentActivity rateBased on the policy results, security alerts are triggered. Defender for Cloud Apps looks at every user session on your cloud and alerts you when something happens that is different from the baseline of your organization or from the user's regular activity.In addition to native Defender for Cloud Apps alerts, you'll also get the following detection alerts based on information received from Microsoft Entra ID Protection:Leaked credentials: Triggered when a user's valid credentials have been leaked. For more information, see Microsoft Entra ID's Leaked credentials detection.Risky sign-in: Combines a number of Microsoft Entra ID Protection sign-in detections into a single detection. For more information, see Microsoft Entra ID's Sign-in risk detections.These policies will appear on the Defender for Cloud Apps policies page and can be enabled or disabled.Anomaly detection policiesYou can see the anomaly detection policies in the Microsoft Defender Portal, by going to Cloud Apps -> Policies -> Policy management. Then choose Anomaly detection policy for the policy type.The following anomaly detection policies are available:Impossible travelThis detection identifies two user activities (in a single or multiple sessions) originating from geographically distant locations within a time period shorter than the time it would have taken the user to travel from the first location to the second, indicating that a different user is using the same credentials. This detection uses a machine-learning algorithm that ignores obvious "false positives" contributing to the impossible travel condition, such as VPNs and locations regularly used by other users in the organization. The detection has an initial learning period of seven days during which it learns a new user's activity pattern. The impossible travel detection identifies unusual and impossible user activity between two locations. The activity should be unusual enough to be considered an indicator of compromise and worthy of an alert. To make thisComments
Different with your account recently, follow these steps to review your account security: Sign in to the Security basics page for your Microsoft account. Select Review activity to check for any unusual sign-in attempts on the Recent activity page. If you see account activity that you're sure wasn't yours, let us know and we can help secure your account—if it's in the Unusual activity section, you can expand the activity and select This wasn't me. If it's in the Recent activity section, you can expand the activity and select Secure your account. If you think someone else may have accessed your account, go back to the Security basics page and select Change password. Create a strong password that you can remember, and don't share it with anybody else. If you tried to sign in to your account but can't, someone may have changed your password. Follow these steps to get back into your account: Try to reset your password with the instructions listed in When you can't sign in to your Microsoft account. Starting with this step saves you extra effort if you accidentally signed in with a different account than the alert was for. If that doesn't work, try to sign in to your account again. Select Forgot my password on the sign-in page, and then select I think someone else is using my Microsoft account. Follow the instructions to recover your account. See also I think my account's been compromised My username and password have stopped working I can't sign in to my Microsoft account How to keep your Microsoft account safe and secure. Unblock my Outlook.com account Account security tools Need more help? Can't sign in? If you can't sign into your Microsoft account, most issues can be identified by our sign-in helper tool.Sign-in helper Contact Support For technical support, go to Contact Microsoft Support, enter your problem and select Get Help. If you still need help, select Contact Support to be routed to the best support option. Important: To protect your account and its contents, our support agents are not allowed to send password reset links, or access and change account details. Need more help? Want more options? Explore subscription benefits, browse training courses, learn how to secure your device, and more.
2025-04-04AgentActivity rateBased on the policy results, security alerts are triggered. Defender for Cloud Apps looks at every user session on your cloud and alerts you when something happens that is different from the baseline of your organization or from the user's regular activity.In addition to native Defender for Cloud Apps alerts, you'll also get the following detection alerts based on information received from Microsoft Entra ID Protection:Leaked credentials: Triggered when a user's valid credentials have been leaked. For more information, see Microsoft Entra ID's Leaked credentials detection.Risky sign-in: Combines a number of Microsoft Entra ID Protection sign-in detections into a single detection. For more information, see Microsoft Entra ID's Sign-in risk detections.These policies will appear on the Defender for Cloud Apps policies page and can be enabled or disabled.Anomaly detection policiesYou can see the anomaly detection policies in the Microsoft Defender Portal, by going to Cloud Apps -> Policies -> Policy management. Then choose Anomaly detection policy for the policy type.The following anomaly detection policies are available:Impossible travelThis detection identifies two user activities (in a single or multiple sessions) originating from geographically distant locations within a time period shorter than the time it would have taken the user to travel from the first location to the second, indicating that a different user is using the same credentials. This detection uses a machine-learning algorithm that ignores obvious "false positives" contributing to the impossible travel condition, such as VPNs and locations regularly used by other users in the organization. The detection has an initial learning period of seven days during which it learns a new user's activity pattern. The impossible travel detection identifies unusual and impossible user activity between two locations. The activity should be unusual enough to be considered an indicator of compromise and worthy of an alert. To make this
2025-04-21Applies ToMicrosoft account dashboard Microsoft prioritizes account security and works to prevent people from signing in without your permission. When we notice a sign-in attempt from a new location or device, we help protect the account by sending you an email message and an SMS alert. If your phone number or email changes, it's important to promptly update the security contact info on the Security basics page so we can work with you to keep your account secure and active. If someone has accessed your account If you think someone has accessed your account, check your Recent activity page and let us know if it wasn't you. Learn what to do if your username and password have stopped working. If you sign in to your account while traveling or if you install a new app that signs in with your account, you may get an alert. We just need you to provide a security code so we know it was you, and that your account is safe. To learn what you can do about unusual activity, select one of the following headings. It'll open to show more info. If there was an unusual sign-in attempt for your account, you'll get an email or text message. We'll send a message to all your alternate contact methods. To help protect your account, we'll need you to provide a security code from one of these contacts. This step prevents people who aren't you from signing in and lets us know if it was just you signing in from an unusual location or device. If you aren't sure about the source of an email, check the sender. You'll know it's legitimate if it's from the Microsoft account team at account-security-noreply@accountprotection.microsoft.com. We may have blocked your sign-in if you're using a new device, if you installed a new app, or if you're traveling or in any new location. This security measure helps keep your account safe in case someone else gets your account information and tries to sign in as you. To unlock your account, follow the instructions on the sign-in screen and select where we can send you a security code. After you've received the code, enter it to access your account. Notes: If you're traveling and can't access the email or phone that you've associated with your account, there are some other options: If these options aren't available, you'll be able to get back in to your account after you sign in from a trusted device or from a usual location. If you brought a device you normally sign in to and you've set it as a trusted device, you can sign in from that device and get back into your account. If you left your phone at home and know someone who has access to it, you can ask them to tell you the security code sent to the device. If you received an email or text alerting you to an unusual sign-in attempt on your account but you haven't done anything
2025-04-19From Washington, the location might show the sign-in coming from California. This is why it helps to check more details about the sign-in, such as the operating system, browser, and app to confirm if it’s actually bad activity.An Unsuccessful sign-in, which shows no session activity, means that primary authentication (username/password) failed. This could mean that the user mistyped their password or an attacker was trying to guess the password. If it’s because an attacker was trying to guess the password (but was unsuccessful), then there’s no need for the user to change their password. However, this is a great reason for the user to register for Azure Multi-Factor Authentication (MFA), so even if the hacker eventually guesses the password, it won’t be enough to access the account. Based on our studies, accounts protected by MFA are 99.9 percent less likely to be compromised.An Unsuccessful sign-in, which shows Session activity of “Additional verification failed, invalid code,” means that primary authentication (username/password) succeeded, but MFA failed. If it was an attacker, they correctly guessed the password but were unable to pass the MFA challenge—such as round tripping a code to a phone number or by using the Microsoft Authenticator app. In this case, the user should still change their password (since the attacker got it right) and go to the Security info page to update their security settings.You can use the Search bar at the top to filter sign-ins by state, country, browser, operating system, app, or account. For example, below I filtered sign-ins in to the My Groups app:In the future, we’ll add This wasn’t me and This was me buttons. We’ll also highlight unusual activities detected with Identity Protection. This user feedback will help improve the accuracy of our risk detection systems. We do all of this already with the
2025-04-01